If you’re like me and had a difficult time at first understanding how to present separate VSAN fabrics to a server in a single vPC, I hope this post helps you out. I’ll be covering this exact scenario, as well as multihop FCoE with Nexus 5K switches in two topologies – Without NPV/NPIV and with NPV/NPIV.
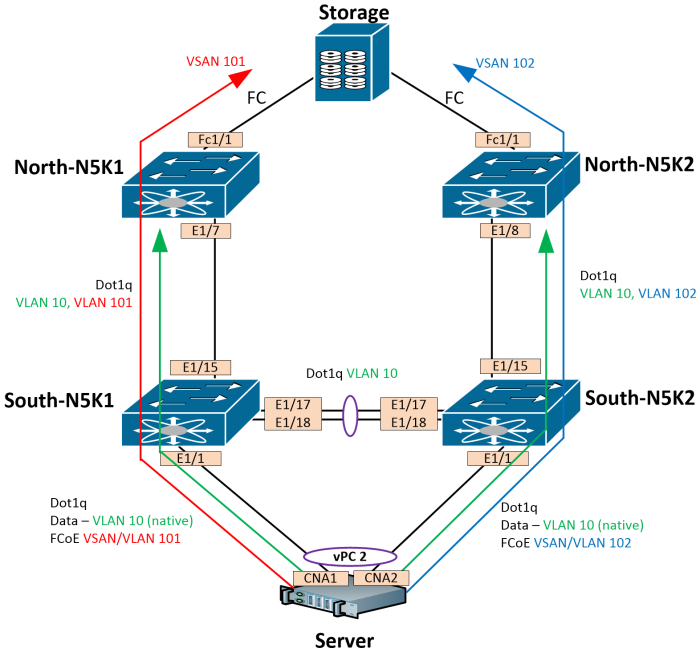
You can run ethernet and FCoE from a server in a vPC connected to two switches. The ethernet portion of the CNA will look like a port-channel, and the fibre channel portion will look like separate connection to separate fabrics. In this topology, we have 1 northbound storage device, 2 north switches, 2 south switches, and an server connected with CNAs. Our end goal is to present the left-side A fabric of our storage device to the server on CNA1 via VSAN 101, and present the right-side B fabric of our storage device to the server on CNA2 via VSAN 102. The server should be in a vPC to both south switches, using VLAN 10 for Data, and separate VSANs for each CNA. All switches should participate in the fabric (no NPV or NPIV).
Our topology looks like this:
When building an FCoE network, VSANs are mapped to FCoE-enabled VLANs that our Ethernet trunks carry between devices. A Virtual Fibre Channel (vfc) interface is built and bonded to the same physical Ethernet interface that carries our FCoE VLAN. These are one-to-one vfc-to-physical-interface mappings. You can also bind vfc interfaces to port-channel interfaces. These vfc interfaces are configured the same way an fc interface is configured; you can set the switchport mode, do vsan trunking, and so on. The image below shows the vfc interfaces with their bindings.
Data VLAN is 10
Fabric A FCoE VLAN is 101, which maps to VSAN 101
Fabric B FCoE VLAN is 102, which maps to VSAN 102
I’m going to configure this with all 4 switches participating in the FC fabric, then I’m going to show the configuration for this with NPV. Configuring FCoE VLANs and the vfc interfaces that connect between switches is a rather straight-forward process. For our particular setup, here are the steps we’ll be following:
FCoE Infrastructure between switches:
1. Enable the fcoe feature
2. Create the VSAN
3. Create the FCoE VLAN, associate it to the VSAN
4. Configure your ports to carry the new FCoE VLAN
5. Configure the vfc interface, bind it to the necessary port
vPC to Server
1. Enable the vPC feature
2. Configure vPC between switches
3. Configure vPC to server
3a. Trunk all VLANs, set the native to the VLAN we are using for Data
3b. Ensure spanning-tree port type edge trunk is configured
vFC to Server
1. Configure the vfc interface to be used as the F_Port to the server
2. Add the vfc to the vsan database for the fabric-specific VSAN
3a. (Option 1) Bind the vfc interface to the vPC port-channel interface facing the server
3b. (Option 2) Bind the vfc interface to the physical Ethernet interface facing the server
4. Verify
Configure the FCoE Infrastructure between switches.
Since the focus is FCoE, we will assume that VLAN 10 (used for regular server data traffic) already exists.
North-N5K1
feature fcoe
vsan database
vsan 101
vsan 101 interface fc1/1
vlan 101
fcoe vsan 101
interface e1/7
switchport mode trunk
switchport trunk allowed vlan 10,101
no shut
interface vfc1
switchport trunk mode e
switchport trunk allowed vsan 101
bind interface e1/1
no shut
North-N5K2
feature fcoe
vsan database
vsan 102
vsan 102 interface fc1/1
vlan 102
fcoe vsan 102
interface e1/8
switchport mode trunk
switchport trunk allowed vlan 10,102
no shut
interface vfc1
switchport trunk mode e
switchport trunk allowed vsan 102
bind interface e1/1
no shut
South-N5K1
feature fcoe
vsan database
vsan 101
vlan 101
fcoe vsan 101
interface e1/15
switchport mode trunk
no shut
interface vfc1
switchport trunk mode e
switchport trunk allowed vsan 101
bind interface e1/15
no shut
South-N5K2
feature fcoe
vsan database
vsan 102
vlan 102
fcoe vsan 102
interface e1/15
switchport mode trunk
no shut
interface vfc1
switchport trunk mode e
switchport trunk allowed vsan 102
bind interface e1/15
no shut
Let’s verify a few things.
Notice on South-N5K1, our vfc interface is up, trunking VSAN 101, and the port is in TE mode. This is also known as a VE port since we’re using virtual fibre channel interfaces, but vFCs support trunking so the port shows as TE. Since we’re trunking, the port VSAN (1) doesn’t matter, just need to make sure that our actual VSAN (101) is up.
South-N5K1(config-if)# show interface vfc1
vfc1 is trunking (Not all VSANs UP on the trunk)
Bound interface is Ethernet1/15
Hardware is Ethernet
Port WWN is 20:00:00:05:73:cd:da:3f
Admin port mode is E, trunk mode is on
snmp link state traps are enabled
Port mode is TE
Port vsan is 1
Trunk vsans (admin allowed and active) (1,101)
Trunk vsans (up) (101)
Trunk vsans (isolated) ()
Trunk vsans (initializing) (1)
1 minute input rate 17272 bits/sec, 2159 bytes/sec, 10 frames/sec
1 minute output rate 16088 bits/sec, 2011 bytes/sec, 10 frames/sec
634 frames input, 82320 bytes
0 discards, 0 errors
636 frames output, 77092 bytes
0 discards, 0 errors
last clearing of "show interface" counters Sat Aug 23 23:10:25 2014
South-N5K1(config-if)# show interface vfc1 brief
-------------------------------------------------------------------------------
Interface Vsan Admin Admin Status Bind Oper Oper
Mode Trunk Info Mode Speed
Mode (Gbps)
-------------------------------------------------------------------------------
vfc1 1 E on trunking Ethernet1/15 TE 10
South-N5K2 is looking good as well, trunking VSAN 102
South-N5K2(config)# show interface vfc1
vfc1 is trunking (Not all VSANs UP on the trunk)
Bound interface is Ethernet1/16
Hardware is Ethernet
Port WWN is 20:00:54:7f:ee:30:4c:bf
Admin port mode is E, trunk mode is on
snmp link state traps are enabled
Port mode is TE
Port vsan is 1
Trunk vsans (admin allowed and active) (1,102)
Trunk vsans (up) (102)
Trunk vsans (isolated) ()
Trunk vsans (initializing) (1)
1 minute input rate 11800 bits/sec, 1475 bytes/sec, 11 frames/sec
1 minute output rate 10352 bits/sec, 1294 bytes/sec, 11 frames/sec
942 frames input, 123312 bytes
0 discards, 0 errors
944 frames output, 109176 bytes
0 discards, 0 errors
last clearing of "show interface" counters Sun Aug 24 03:12:59 2014
Interface last changed at Sun Aug 24 03:13:03 2014
South-N5K2(config)# show interface vfc1 bri
-------------------------------------------------------------------------------
Interface Vsan Admin Admin Status Bind Oper Oper
Mode Trunk Info Mode Speed
Mode (Gbps)
-------------------------------------------------------------------------------
vfc1 1 E on trunking Ethernet1/16 TE 10
Assuming zoning is configured, all 4 switches can now see the active zoneset.
Configure vPC between switches and to the server
South-N5K1:
feature vpc
vpc domain 1
peer-keepalive destination 10.255.255.2
interface e1/17-18
channel-group 1 mode active
no shut
interface po1
switchport mode trunk
switchport trunk allowed vlan 10
vpc peer-link
no shut
# To Server
interface e1/1
channel-group 2 mode active
no shut
interface po2
switchport mode trunk
switchport trunk allowed vlan all
switchport trunk native vlan 10
spanning-tree port type edge trunk
vpc 2
no shut
South-N5K2:
feature vpc
vpc domain 1
peer-keepalive destination 10.255.255.1
interface e1/17-18
channel-group 1 mode active
no shut
interface po1
switchport mode trunk
switchport trunk allowed vlan 10
vpc peer-link
no shut
# To Server
interface e1/1
channel-group 2 mode active
no shut
interface po2
switchport mode trunk
switchport trunk allowed vlan all
switchport trunk native vlan 10
spanning-tree port type edge trunk
vpc 2
no shut
Port-channel is up, trunking all VLANs, native is VLAN 10. Note, you cannot set FCoE VLAN as a native, this is unsupported and will not operate.
South-N5K1(config-if)# show interface port-channel 2 switchport
Name: port-channel2
Switchport: Enabled
Switchport Monitor: Not enabled
Operational Mode: trunk
Access Mode VLAN: 1 (default)
Trunking Native Mode VLAN: 10 (VLAN10)
Trunking VLANs Allowed: 1-4094
South-N5K1(config)# show vpc 2
vPC status
----------------------------------------------------------------------------
id Port Status Consistency Reason Active vlans
------ ----------- ------ ----------- -------------------------- -----------
2 Po2 up success success 1,10,101
South-N5K2(config)# show vpc 2
vPC status
----------------------------------------------------------------------------
id Port Status Consistency Reason Active vlans
------ ----------- ------ ----------- -------------------------- -----------
2 Po2 up success success 1,10,102
Configure vFC interfaces to Server
Just to show that you have options, I’ll bind South-N5K1’s vfc to the port-channel, and South-N5K2’s vfc to the physical interface. Because this is not an E_Port, we need to ensure that we add this interface to the correct VSAN in the VSAN database.
South-N5K1
interface vfc2
vsan database
vsan 101 interface vfc2
interface vfc2
bind interface po2
no shut
South-N5K2
interface vfc2
vsan database
vsan 102 interface vfc2
interface vfc2
bind interface e1/1
no shut
We now have a FLOGI from the server on South-N5K1 VSAN 101
South-N5K1(config-if)# show flogi database
--------------------------------------------------------------------------------
INTERFACE VSAN FCID PORT NAME NODE NAME
--------------------------------------------------------------------------------
vfc2 101 0x450000 21:00:00:b0:cc:02:c0:f9 20:00:00:b0:cc:02:c0:f9
Total number of flogi = 1.
The vFC is in VSAN 101, and it is up. Port is in TF mode
South-N5K1(config)# show interface vfc2
vfc2 is trunking (Not all VSANs UP on the trunk)
Bound interface is port-channel2
Hardware is Ethernet
Port WWN is 20:01:00:05:73:cd:da:3f
Admin port mode is F, trunk mode is on
snmp link state traps are enabled
Port mode is TF
Port vsan is 101
Trunk vsans (admin allowed and active) (1,101)
Trunk vsans (up) (101)
Trunk vsans (isolated) ()
Trunk vsans (initializing) (1)
1 minute input rate 384 bits/sec, 48 bytes/sec, 0 frames/sec
1 minute output rate 848 bits/sec, 106 bytes/sec, 0 frames/sec
135 frames input, 15952 bytes
0 discards, 0 errors
221 frames output, 35048 bytes
0 discards, 0 errors
last clearing of "show interface" counters Sat Aug 23 23:37:12 2014
We have a FLOGI on South-N5K2 VSAN 102 from the server
South-N5K2(config)# show flogi database
--------------------------------------------------------------------------------
INTERFACE VSAN FCID PORT NAME NODE NAME
--------------------------------------------------------------------------------
vfc2 102 0x380000 21:00:00:b0:cc:02:c0:fb 20:00:00:b0:cc:02:c0:fb
Total number of flogi = 1.
The vFC is up and on VSAN 102
South-N5K2(config)# show interface vfc2
vfc2 is trunking (Not all VSANs UP on the trunk)
Bound interface is Ethernet1/1
Hardware is Ethernet
Port WWN is 20:01:54:7f:ee:30:4c:bf
Admin port mode is F, trunk mode is on
snmp link state traps are enabled
Port mode is TF
Port vsan is 102
Trunk vsans (admin allowed and active) (1,102)
Trunk vsans (up) (102)
Trunk vsans (isolated) ()
Trunk vsans (initializing) (1)
1 minute input rate 1336 bits/sec, 167 bytes/sec, 1 frames/sec
1 minute output rate 1616 bits/sec, 202 bytes/sec, 1 frames/sec
75 frames input, 10052 bytes
0 discards, 0 errors
103 frames output, 12704 bytes
0 discards, 0 errors
last clearing of "show interface" counters Sun Aug 24 03:36:28 2014
We now have Multihop FCoE running, with split VSAN fabrics in a vPC. Awesome!
Configuring NPV / NPIV
In the above example, all switches particpated in the fabric, each had an FC Domain ID and each had zoning configured. To reduce complexity and simplify configuration, we can implement NPV and NPIV.
NPV is N_Port Virtualization. A switch running in this mode does not participate in fibre channel intelligence, it simply proxies host FLOGIs to another switch in the fabric with intelligence. There is NO zoning on an NPV switch, and no FLOGI database since FLOGIs are now proxied north to an NPIV switch. This NPV switch now appears to the fabric as a Node Proxy Port (NP_Port).
NPIV is N_Port ID Virtualization. A switch running in this mode will accept connections to NP_Ports, and allow multiple FLOGIs from that single port. An NPV switch must connect to an NPIV-enabled switch. All hosts that FLOGI now show up logged into the NPIV switch above the NPV switch.
NPV is supported northbound over FCoE. The VE-to-VE port turns into a VNP-to-VF port connection.
Let’s configure the two North switches to run NPIV:
North-N5K1
feature fcoe
feature npiv
vsan database
vsan 101
vsan 101 interface fc1/1
vlan 101
fcoe vsan 101
interface vfc4
bind interface Ethernet1/7
switchport trunk mode f
switchport trunk allowed vsan 101
no shutdown
interface Ethernet1/7
switchport mode trunk
North-N5K2
feature fcoe
feature npiv
vsan database
vsan 102
vsan 102 interface fc1/1
vlan 102
fcoe vsan 102
interface vfc4
bind interface Ethernet1/7
switchport trunk mode f
switchport trunk allowed vsan 102
no shutdown
interface Ethernet1/8
switchport mode trunk
And the two South switches in NPV mode
South-N5K1
feature fcoe-npv
vsan database
vsan 101
vlan 101
fcoe vsan 101
interface vfc1
switchport mode np
bind interface e1/15
no shut
South-N5K2
feature fcoe-npv
vsan database
vsan 102
vlan 102
fcoe vsan 102
interface vfc1
switchport mode np
bind interface e1/15
no shut
Verify our vFC interface is up on South-N5K1, it’s in TNP mode (Same as VNP), the important part is NP (Node Proxy).
South-N5K1(config)# show interface vfc1
vfc1 is trunking (Not all VSANs UP on the trunk)
Bound interface is Ethernet1/15
Hardware is Ethernet
Port WWN is 20:00:00:05:73:cd:da:3f
Admin port mode is NP, trunk mode is on
snmp link state traps are enabled
Port mode is TNP
Port vsan is 1
Trunk vsans (admin allowed and active) (1,101)
Trunk vsans (up) (101)
Trunk vsans (isolated) ()
Trunk vsans (initializing) (1)
1 minute input rate 488 bits/sec, 61 bytes/sec, 0 frames/sec
1 minute output rate 232 bits/sec, 29 bytes/sec, 0 frames/sec
13 frames input, 2008 bytes
0 discards, 0 errors
7 frames output, 1004 bytes
0 discards, 0 errors
last clearing of "show interface" counters Sat Aug 23 15:20:55 2014
Notice we can no longer see the zoning configuration; no zoning in NPV mode.
South-N5K1(config)# show zoneset active
^
% Invalid command at '^' marker.
The switch north of the NPV has it’s port in TF mode now instead of TE. No longer an expansion, this is now a Fabric port.
North-N5K1# show interface vfc4
vfc4 is trunking
Bound interface is Ethernet1/7
Hardware is Virtual Fibre Channel
Port WWN is 20:03:00:05:9b:25:d7:ff
Admin port mode is F, trunk mode is on
snmp link state traps are enabled
Port mode is TF
Port vsan is 1
Trunk vsans (admin allowed and active) (101)
Trunk vsans (up) (101)
Trunk vsans (isolated) ()
Trunk vsans (initializing) ()
1 minute input rate 8 bits/sec, 1 bytes/sec, 0 frames/sec
1 minute output rate 24 bits/sec, 3 bytes/sec, 0 frames/sec
1405716 frames input, 147126848 bytes
0 discards, 0 errors
1411357 frames output, 186070436 bytes
0 discards, 0 errors
last clearing of "show interface" counters never
Notice we already have on FLOGI, which is from the South-N5K1 switch itself logging into the fabric via it’s NP_Port:
North-N5K1# show flogi database interface vfc4
--------------------------------------------------------------------------------
INTERFACE VSAN FCID PORT NAME NODE NAME
--------------------------------------------------------------------------------
vfc4 101 0x170002 20:00:00:05:73:cd:da:3f 20:0b:00:05:73:cd:da:01
Total number of flogi = 1.
North-N5K1# show interface e1/7 fcoe
Ethernet1/7 is FCoE UP
vfc4 is Up
FCID is 0x170003
PWWN is 21:00:00:b0:cc:02:c0:f9
MAC addr is 00:c0:dd:13:d1:f9
FCID is 0x170002
PWWN is 20:00:00:05:73:cd:da:3f
MAC addr is 00:05:73:cd:da:16
The other side looks the same, except VSAN 102, so I won’t clutter up this post with the output.
Configure the port from the NPV switch to the server.
South-N5K1:
conf t
interface vfc2
vsan database
vsan 101 interface vfc2
interface vfc2
bind interface po2
no shut
Check out the FLOGI database on South-N5K1
South-N5K1(config-if)# show flogi database
^
% Invalid command at '^' marker.
Since logins are proxied to the core, this command is no longer exists. To see this, run “show npv flogi”.
South-N5K1(config-if)# show npv flogi
--------------------------------------------------------------------------------
SERVER EXTERNAL
INTERFACE VSAN FCID PORT NAME NODE NAME INTERFACE
--------------------------------------------------------------------------------
vfc2 101 0x170003 21:00:00:b0:cc:02:c0:f9 20:00:00:b0:cc:02:c0:f9 vfc1
Total number of flogi = 1.
Let’s check out our vFC interface to the server. We can see that it is a TF port
South-N5K1(config-if)# show interface vfc2
vfc2 is trunking (Not all VSANs UP on the trunk)
Bound interface is port-channel2
Hardware is Ethernet
Port WWN is 20:01:00:05:73:cd:da:3f
Admin port mode is F, trunk mode is on
snmp link state traps are enabled
Port mode is TF
Port vsan is 101
Trunk vsans (admin allowed and active) (1,101)
Trunk vsans (up) (101)
Trunk vsans (isolated) ()
Trunk vsans (initializing) (1)
1 minute input rate 336 bits/sec, 42 bytes/sec, 0 frames/sec
1 minute output rate 816 bits/sec, 102 bytes/sec, 0 frames/sec
332 frames input, 114000 bytes
0 discards, 0 errors
684 frames output, 639068 bytes
0 discards, 0 errors
last clearing of "show interface" counters Sat Aug 23 15:26:04 2014
And hey, we now have two FLOGIs on our North-N5K1 switch, coming from the same port with two different nWWNs
North-N5K1# show flogi database interface vfc4
--------------------------------------------------------------------------------
INTERFACE VSAN FCID PORT NAME NODE NAME
--------------------------------------------------------------------------------
vfc4 101 0x170002 20:00:00:05:73:cd:da:3f 20:0b:00:05:73:cd:da:01
vfc4 101 0x170003 21:00:00:b0:cc:02:c0:f9 20:00:00:b0:cc:02:c0:f9
Total number of flogi = 2.
Lastly, we’ll get South-N5K2 up to speed
South-N5K2:
interface vfc2
vsan database
vsan 102 interface vfc2
interface vfc2
bind interface po2
no shut
The server sent it’s FLOGI
South-N5K2(config)# show npv flogi-table
--------------------------------------------------------------------------------
SERVER EXTERNAL
INTERFACE VSAN FCID PORT NAME NODE NAME INTERFACE
--------------------------------------------------------------------------------
vfc2 102 0x170003 21:00:00:b0:cc:02:c0:fb 20:00:00:b0:cc:02:c0:fb vfc1
Total number of flogi = 1.
And the North NPIV-enabled switch received the proxied FLOGI from the South NPV switch.
North-N5K2# show flogi database interface vfc4
--------------------------------------------------------------------------------
INTERFACE VSAN FCID PORT NAME NODE NAME
--------------------------------------------------------------------------------
vfc4 102 0x170003 21:00:00:b0:cc:02:c0:fb 20:00:00:b0:cc:02:c0:fb
vfc4 102 0x17002a 20:00:54:7f:ee:30:4c:bf 20:0c:54:7f:ee:30:4c:81
Total number of flogi = 2.
We have configured Multihop NPV/NPIV FCoE with split VSANs in a vPC.
Additional Notes
QoS
Make sure qos is set properly after enabling fcoe:
system qos
service-policy type qos input fcoe-default-in-policy
service-policy type queuing input fcoe-default-in-policy
service-policy type queuing output fcoe-default-out-policy
service-policy type network-qos fcoe-default-nq-policy
Hashing
For more efficient load distribution, change the port-channel load-balancing to include port instead of mac (which would only use one port)
port-channel load-balance ethernet source-dest-port
Quick Template
Here is a quick template just showing the South switches
South-N5K1 | South-N5K2
|
feature fcoe | feature fcoe
vsan database | vsan database
vsan 101 | vsan 102
vlan 101 | vlan 102
fcoe vsan 101 | fcoe vsan 102
int vfc1 | int vfc1
switchport mode e | switchport mode e
bind interface e1/15 | bind interface e1/16
no shut | no shut
|
# Configure vPC | # Configure vPC
|
feature vpc | feature vpc
vpc domain 1 | vpc domain 1
peer-keepalive destination 10.255.255.1 | peer-keepalive destination 10.255.255.2
! | !
interface e1/17-18 | interface e1/17-18
channel-group 1 mode active | channel-group 1 mode active
no shut | no shut
interface po1 | interface po1
switchport mode trunk | switchport mode trunk
switchport trunk allowed vlan 10 | switchport trunk allowed vlan 10
vpc peer-link | vpc peer-link
no shut | no shut
|
# To Server | # To Server
|
interface e1/1 | interface e1/1
channel-group 2 mode active | channel-group 2 mode active
no shut | no shut
interface po2 | interface po2
switchport mode trunk | switchport mode trunk
switchport trunk allowed vlan all | switchport trunk allowed vlan all
switchport trunk native vlan 10 | switchport trunk native vlan 10
spanning-tree port type edge trunk | spanning-tree port type edge trunk
vpc 2 | vpc 2
no shut | no shut
|
# Configure vFC down to the server | # Configure vFC down to the server
|
interface vfc2 | interface vfc2
vsan database | vsan database
vsan 101 interface vfc2 | vsan 102 interface vfc2
interface vfc2 | interface vfc2
bind interface po2 | bind interface po2
no shut | no shut
|
# If running NPV | # If running NPV
|
feature fcoe-npv | feature fcoe-npv
int vfc2 | int vfc2
switchport mode f | switchport mode f
Helpful show commands
show vlan fcoe
show int vfc1
show int vfc1 brief
show zoneset active
show flogi database
show npv flogi
show interface vfc2
show interface vfc2 brief





David – thanks for posting this information. I had been following the Cisco NX-OS FCoE Configuration Guide, but my vFC wasn’t coming up and doing an FLOGI. I followed your setup flow and – success!
That’s great news, Steve! Glad I could help a fellow Engineer out.
This is a great guide, but the interface numbers on your diagram do not match up with the interface numbers used in your configuration snippets which made it difficult to follow.
Matt – How embarrassing, you are right! I have corrected the templates, and all interfaces should now match what is in the drawing. The only discrepancy is with E1/15 on South-N5K2. This is actually E1/16 as you may see in some of the output. Thanks for pointing this out!
On the first topology (without NPV) you have vfc interfaces to the disk and to the server, but not between the 5Ks. Thus you have two separate fabrics, correct? I believe this is corrected in the NPV topology.
Yes, there are two separate fabrics. Vfc’s do exist from north-to-south 5Ks, but not east-to-west.
Hi David, thank You very much for such a good and detailed explanation ! very nice explained ! I really love Your drawings as well as they are very clear !
Which icon file`s You have used in the drawings above ? could You please send it to me via email ?
Thanks for the kind comment! I’m using the stencils that can be found here: http://www.visiocafe.com/vsdfx.htm
You`re welcome, thank You for icon sharing !
David, thanks for the great documentation. We have a setup similar to the NPIV/NPV design you describe above. We are looking at some blade solutions which require NPIV to be enabled on the south switches. We are working towards decommissioning our “north” Brocade switches and going to Cisco N7Ks. Because of this, we want to have uplinks for the new blades go to our “south” Cisco N5Ks. The N5Ks are in NPV mode, so only one blade can see the SAN at the time. Can we enable NPIV on the Cisco N5Ks for downstream connections (blades) and continue to use NPV for upstream connections (other servers connected to N5Ks plus blades) to the Brocades and eventually the Cisco N7Ks? Basically, can the N5Ks allow multiple FC IDs on a port and then relay those all to the north switch as individual servers?
David
Thanks a lot for great article. it clarify many of my doubts !
Just small clarification, should the mode toward server as “F”, instead of “NP ?
# If running NPV | # If running NPV
|
feature fcoe-npv | feature fcoe-npv
int vfc2 | int vfc2
switchport mode np | switchport mode np
or i miss something here
Yes, you are correct! That must have been an error on my part. I have corrected the error. Apologies for the confusion.
Hi david,
thank you for your great post, just to clarify. on your first section post without NPV/NPIV mode, the Vfc1 interface on north5k should bind to int e1/7 and e1/8 respectively.